Hackers are targeting WordPress sites of all sizes – it’s not just the big guys. However, there are many steps you can take to ensure a more secure WordPress environment. The following article outlines 13 useful WordPress security tips to help keep your website safe.
We know WordPress Security
WordPress is an excellent platform for managing your website, which is why it has grown to become the most popular Content Management System (CMS) for site owners on the web. However, its tremendous growth over the years has also drawn the attention of hackers who are looking to target vulnerable WordPress sites. In a digital world that’s becoming only more reliant on the internet and online resources, all website owners need to be vigilant of the WordPress security threats out there and take preventative measures to combat these potential risks. Websites large and small belonging to various industries can be targeted by hackers for any reason – it’s not just the big companies that are targeted. In many cases, smaller, independently owned websites lacking the same level of ongoing technical support are prime destinations for hackers’ brute-force attacks.
What is a “Brute-Force Attack”?
In this context, a brute-force attack is when an attacker submits many passwords, checking all possibilities, in order to eventually guess the correct one to infiltrate a website. Depending on the predefined values for generating a password, brute-force attacks can take several minutes up until several hours, days or even years. However, regardless of time, brute-force attacks have a higher probability of success than most hacking techniques.
Brute-Force Attacks take Place at your WordPress login screen.
How can I protect my site against attacks?
There are many practices a site owner can take to not only prevent these type of attacks, but also reduce the possibility of hackers trying to target a site in the first place. If you manage a WordPress site and are looking for ways to enhance your site’s protection against potential hackers, we recommend these 13 WordPress Security tips in order to more effectively secure your WordPress environment before it’s too late.
1. Updates to WordPress, Themes & Plugins
It’s very important to update WordPress and its plugins on a regular schedule. Over 80% of websites that are hacked become compromised because they were not being updated regularly. Therefore, the more often updates take place, the less possibility for a potential vulnerability to be exposed. Themes, plugins and WordPress platforms that are not up to speed on the current versions are sometimes updated for the sole purpose of filling a hole in security, so not doing so leaves your site much more open to an attack.
2. Backups
If a hacker is able to infiltrate your site, it’s vital to have a plan in place to reduce the total damage. Backups ensure that your site is always safe, and, in the event of a hack, human error, or hosting error, the site will be able to be restored and running quickly. Frequency of backups depends on your maintenance plan.
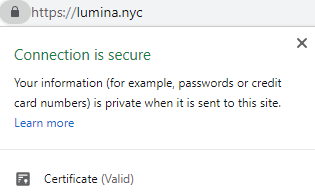
3. SSL & HTTPS
This refers to the process of installing and validating SSL including redirection from all non-https versions. Chrome browser, for example, classifies all websites without SSL as secure and presents this information to the user. HTTPS (or Secure HTTP) is an encryption method that secures the connection between users’ browsers and the site server. SSL is the unique certificate for identification purposes. If you do not have this installed on your site, it could be an instant flag to a potential hacker that your site might have other vulnerabilities. Google announced in 2014 it actually boosts a website’s SEO ranking for adopting HTTPS.
4. User Accounts Limit
Limiting the amount of user accounts possible is a simple but useful tactic. Since brute-force attacks are a result of insecure login credential information, the more user accounts there are, the more potential avenues for gaining access into the site that exist. It’s important to have as minimal user accounts as possible in order to reduce the possibility of these attacks.
5. User Account Roles
We advise that you reduce each user’s roles to the minimal permissions needed in WordPress. WordPress provides six default user roles, each with its own permissions and capacities. It’s important to be consistent in maintaining user roles because it helps reduce the amount of paths to important backend features or sensitive information. For example, it’s not recommended to to give a casual blog contributor access to site plugins. That way, even if a user account’s access was compromised, security threats would not have full access to components of the site.
6. User Login Credentials
Implementing auto-generated passwords and having no users with the name “admin” reduce the risks of any login information being compromised. Since Brute Force Attacks are caused by insecure account login information, the more random passwords are, the more secure they become. Since “admin” is a common username for a site administrator, using something else reduces correct guesses of login credentials.
7. iThemes Premium
Hardening security by utilizing the premium version of iThemes and making adjustments to the WordPress default security settings (404 detection, user/IP banning, file change detection, etc.). If you use the general Secure Site option from iThemes, it will automatically enable some useful security options.
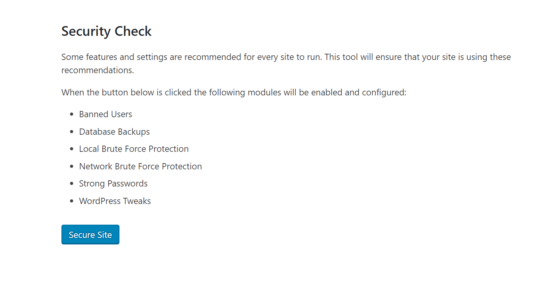
The Secure Site button from iThemes will implement useful security options.
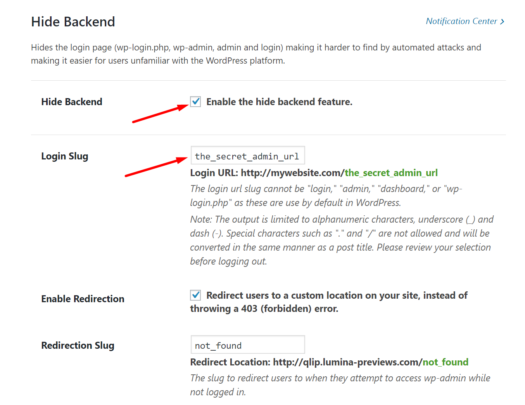
8. Custom URL for Admin
This refers to the process of changing the default /wp-admin to a custom URL. Without changing this, any security threat that is familiar with WordPress would be easily able to access the main location of entry into the site. Changing the URL to something that is hard to guess is a small tweak that – when implemented as part of a comprehensive security plan – makes it more difficult for hackers and spammers to gain access.
9. Two Factor Authentication
Making two factor authentication a requirement for login into WordPress is a useful and smart security practice. This way, even if a security threat obtained login credentials for WordPress, they will still need to enter a security code sent to the user’s phone. This helps greatly reduce the possibility of Brute Force Attacks.
10. wp-config.php Files
Lumina recommends denying wp-config.php and .htaccess file access. WordPress wp-config.php files contain sensitive information about website installation, including items such as security keys, table prefix and database connection details. It’s important to protect the wp-config.php file in order to properly store this sensitive information. By encrypting its content when uploading and then denying access to it, you can prevent this file from getting into the wrong hands.
11. Login Limits
Another useful practice for site security is to create limits for the amount of login attempts, and lock out an IP address after a certain amount of login attempts. This will combat brute-force attacks by preventing a source of security risk unlimited attempts at logging in.
12. XML-RPC
We advise site owners to disable XML-RPC on WordPress. An API that gives site managers the ability to make remote changes to a WP site without logging into the standard admin backend, there are security concerns with the feature. This is because it provides an additional surface for attack if a vulnerability is ever found, and in the past XML-RPC has become an increasingly large target for brute force attacks. Therefore, disabling this feature reduces the amount of paths into the WordPress site.
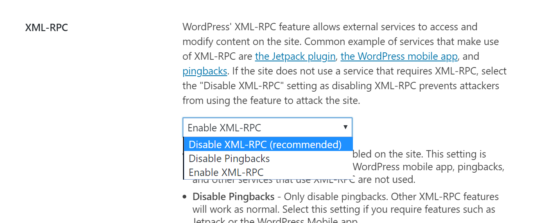
It is better to disable XML-RPC if you are not using these services.
13. 3rd-Party Functionality
Lumina recommends minimal use of 3rd-party plugins. Implementing 3rd-party plugins gives the site additional possibilities of pathways leading back to the site itself. Vulnerabilities in these plugins’ own security could consequently damage the security of the sites using them. By reducing the amount of 3rd-party plugins through custom development of functionality and backend features, you are guaranteeing a lower probability of overall vulnerability.
For more info on the terms discussed in this article, check out our tech dictionary.